Microsoft 365 / Office 365 A1 / A1P / A3 通过 API 提升子号为全局管理员的教程 / 方法
首先,感谢两位大佬的教程
https://hostloc.com/thread-833230-1-1.html
https://hostloc.com/thread-833198-1-1.html
我在他们教程的基础上加以细化,让小白也能上手
为什么要通过 API 提升子号为全局管理员?这个原因其实很简单,了解 Microsoft 365 / Office 365 A1 / A1P / A3 的朋友应该都知道,对于这些来源不明的全局,微软发现后肯定是要封的,封所有管理员,但是一般不封子号,封了后,如果你还有 API,那么就可以通过 API 提升子号为全局管理员,再次对全局进行掌控
一 Microsoft 365 / Office 365 A1 / A1P / A3 通过 API 提升子号为全局管理员的基本条件
- API 权限:RoleManagement.ReadWrite.Directory
- 能登录的子号
- SP 不为 0
满足以上三个条件后,就可以开始提升子号为全局管理员
二 创建 Azure AD 应用程序
可以看我以前的教程:
一定要开启:RoleManagement.ReadWrite.Directory 权限
三 注册 Postman
进入:
注册并登录账号
四 创建 Microsoft Graph Postman 工作区
不明白的请看官方文档:点击进入
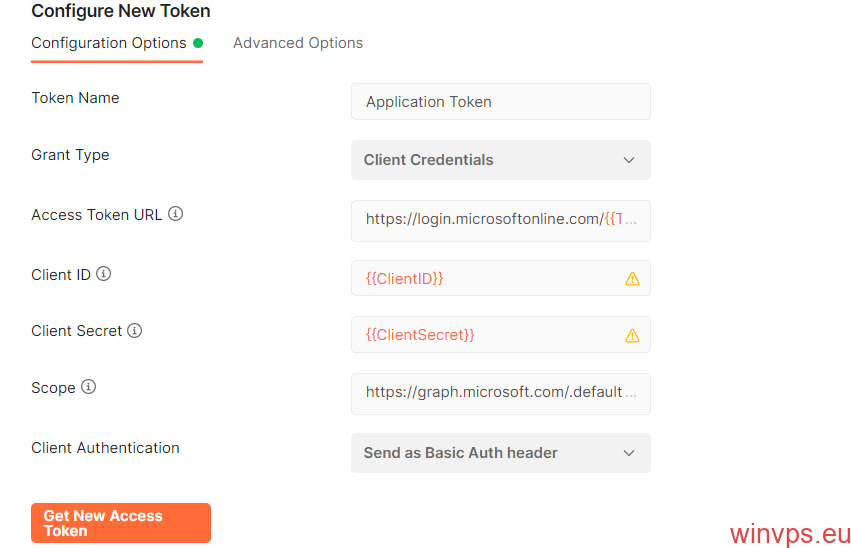
五 在 Postman 中配置身份验证 / 授权
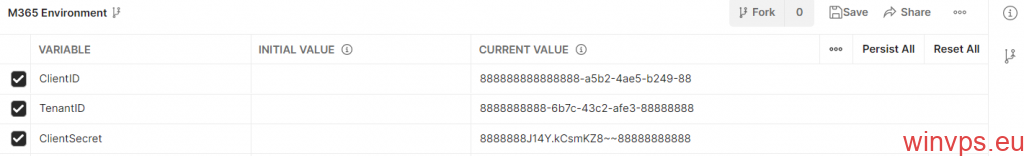
填入第二步中得到的【ClientID】【TenantID】【ClientSecret】,然后点【Save】保存
进入【Application】开始授权
注意上图中右上角那儿要选择刚刚创建的【M365 Environment】
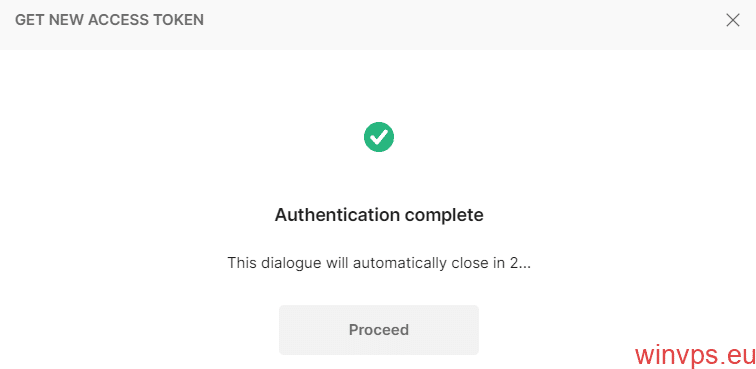
点击【Get New Access Token】开始授权
授权成功
点击【Use Token】后再点击【Save】保存
不明白的请看官方文档:点击进入
六 获取子号 ID & 管理员 ID
进入位置请看下图
在 GET 后输入:
# 输入以下地址 https://graph.microsoft.com/v1.0/users
然后点击【Send】
# 返回结果
{
"businessPhones": [],
"displayName": "GV靓号",
"givenName": "GV",
"jobTitle": null,
"mail": null,
"mobilePhone": null,
"officeLocation": null,
"preferredLanguage": null,
"surname": "靓号",
"userPrincipalName": "[email protected]",
"id": "763b6ba7-549e-4364-bc9f-3f63af52e860"
},
记录要提权为管理员的子号 ID,即最后一行
在 GET 后输入:
# 输入以下地址 https://graph.microsoft.com/v1.0/directoryRoleTemplates
然后点击【Send】
# 返回结果
# 全局管理员
{
"id": "62e90394-69f5-4237-9190-012177145e10",
"deletedDateTime": null,
"description": "Can manage all aspects of Azure AD and Microsoft services that use Azure AD identities.",
"displayName": "Global Administrator"
},
# 密码管理员
{
"id": "966707d0-3269-4727-9be2-8c3a10f19b9d",
"deletedDateTime": null,
"description": "Can reset passwords for non-administrators and Password Administrators.",
"displayName": "Password Administrator"
},
记录要提权为哪种管理员的 ID,即第一行
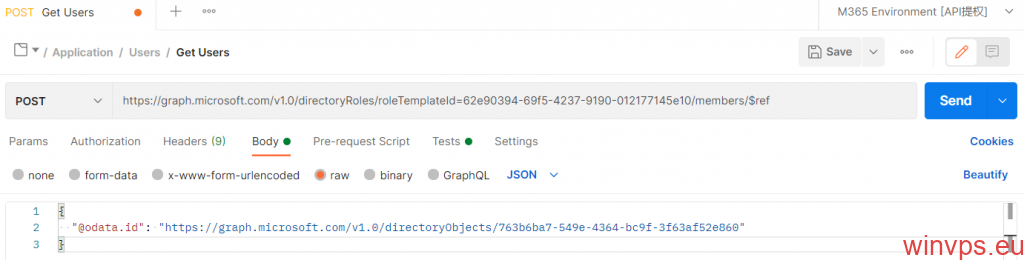
七 Microsoft 365 / Office 365 A1 / A1P / A3 通过 API 提升子号为全局管理员
我以提升为全局管理员为例来示范
# 在 POST 后输入下面的内容,62e90394-69f5-4237-9190-012177145e10 可以修改为其他管理员 ID
https://graph.microsoft.com/v1.0/directoryRoles/roleTemplateId=62e90394-69f5-4237-9190-012177145e10/members/$ref
# 在相应位置输入下面的内容,763b6ba7-549e-4364-bc9f-3f63af52e860 换成你子号的 ID
{
"@odata.id": "https://graph.microsoft.com/v1.0/directoryObjects/763b6ba7-549e-4364-bc9f-3f63af52e860"
}
注意看图中内容的输入位置
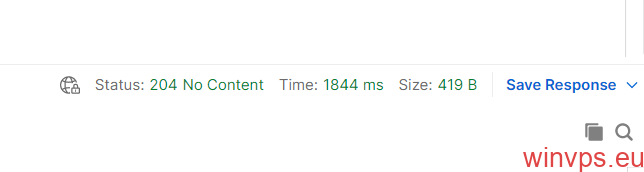
最后点击【Send】
返回【204 No Content】,说明成功了
不明白的请看官方文档:点击进入
Microsoft 365 / Office 365 A1 / A1P / A3 通过 API 提升子号为全局管理员的教程 / 方法结束
所有管理员 ID
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#directoryRoleTemplates",
"value": [
{
"id": "62e90394-69f5-4237-9190-012177145e10",
"deletedDateTime": null,
"description": "Can manage all aspects of Azure AD and Microsoft services that use Azure AD identities.",
"displayName": "Global Administrator"
},
{
"id": "10dae51f-b6af-4016-8d66-8c2a99b929b3",
"deletedDateTime": null,
"description": "Default role for guest users. Can read a limited set of directory information.",
"displayName": "Guest User"
},
{
"id": "2af84b1e-32c8-42b7-82bc-daa82404023b",
"deletedDateTime": null,
"description": "Default role for guest users with restricted access. Can read a limited set of directory information.",
"displayName": "Restricted Guest User"
},
{
"id": "95e79109-95c0-4d8e-aee3-d01accf2d47b",
"deletedDateTime": null,
"description": "Can invite guest users independent of the 'members can invite guests' setting.",
"displayName": "Guest Inviter"
},
{
"id": "fe930be7-5e62-47db-91af-98c3a49a38b1",
"deletedDateTime": null,
"description": "Can manage all aspects of users and groups, including resetting passwords for limited admins.",
"displayName": "User Administrator"
},
{
"id": "729827e3-9c14-49f7-bb1b-9608f156bbb8",
"deletedDateTime": null,
"description": "Can reset passwords for non-administrators and Helpdesk Administrators.",
"displayName": "Helpdesk Administrator"
},
{
"id": "f023fd81-a637-4b56-95fd-791ac0226033",
"deletedDateTime": null,
"description": "Can read service health information and manage support tickets.",
"displayName": "Service Support Administrator"
},
{
"id": "b0f54661-2d74-4c50-afa3-1ec803f12efe",
"deletedDateTime": null,
"description": "Can perform common billing related tasks like updating payment information.",
"displayName": "Billing Administrator"
},
{
"id": "a0b1b346-4d3e-4e8b-98f8-753987be4970",
"deletedDateTime": null,
"description": "Default role for member users. Can read all and write a limited set of directory information.",
"displayName": "User"
},
{
"id": "4ba39ca4-527c-499a-b93d-d9b492c50246",
"deletedDateTime": null,
"description": "Do not use - not intended for general use.",
"displayName": "Partner Tier1 Support"
},
{
"id": "e00e864a-17c5-4a4b-9c06-f5b95a8d5bd8",
"deletedDateTime": null,
"description": "Do not use - not intended for general use.",
"displayName": "Partner Tier2 Support"
},
{
"id": "88d8e3e3-8f55-4a1e-953a-9b9898b8876b",
"deletedDateTime": null,
"description": "Can read basic directory information. Commonly used to grant directory read access to applications and guests.",
"displayName": "Directory Readers"
},
{
"id": "9360feb5-f418-4baa-8175-e2a00bac4301",
"deletedDateTime": null,
"description": "Can read and write basic directory information. For granting access to applications, not intended for users.",
"displayName": "Directory Writers"
},
{
"id": "29232cdf-9323-42fd-ade2-1d097af3e4de",
"deletedDateTime": null,
"description": "Can manage all aspects of the Exchange product.",
"displayName": "Exchange Administrator"
},
{
"id": "f28a1f50-f6e7-4571-818b-6a12f2af6b6c",
"deletedDateTime": null,
"description": "Can manage all aspects of the SharePoint service.",
"displayName": "SharePoint Administrator"
},
{
"id": "75941009-915a-4869-abe7-691bff18279e",
"deletedDateTime": null,
"description": "Can manage all aspects of the Skype for Business product.",
"displayName": "Skype for Business Administrator"
},
{
"id": "d405c6df-0af8-4e3b-95e4-4d06e542189e",
"deletedDateTime": null,
"description": "Device Users",
"displayName": "Device Users"
},
{
"id": "9f06204d-73c1-4d4c-880a-6edb90606fd8",
"deletedDateTime": null,
"description": "Device Administrators",
"displayName": "Azure AD Joined Device Local Administrator"
},
{
"id": "9c094953-4995-41c8-84c8-3ebb9b32c93f",
"deletedDateTime": null,
"description": "Device Join",
"displayName": "Device Join"
},
{
"id": "c34f683f-4d5a-4403-affd-6615e00e3a7f",
"deletedDateTime": null,
"description": "Workplace Device Join",
"displayName": "Workplace Device Join"
},
{
"id": "17315797-102d-40b4-93e0-432062caca18",
"deletedDateTime": null,
"description": "Can read and manage compliance configuration and reports in Azure AD and Office 365.",
"displayName": "Compliance Administrator"
},
{
"id": "d29b2b05-8046-44ba-8758-1e26182fcf32",
"deletedDateTime": null,
"description": "Only used by Azure AD Connect service.",
"displayName": "Directory Synchronization Accounts"
},
{
"id": "2b499bcd-da44-4968-8aec-78e1674fa64d",
"deletedDateTime": null,
"description": "Deprecated - Do Not Use.",
"displayName": "Device Managers"
},
{
"id": "9b895d92-2cd3-44c7-9d02-a6ac2d5ea5c3",
"deletedDateTime": null,
"description": "Can create and manage all aspects of app registrations and enterprise apps.",
"displayName": "Application Administrator"
},
{
"id": "cf1c38e5-3621-4004-a7cb-879624dced7c",
"deletedDateTime": null,
"description": "Can create application registrations independent of the 'Users can register applications' setting.",
"displayName": "Application Developer"
},
{
"id": "5d6b6bb7-de71-4623-b4af-96380a352509",
"deletedDateTime": null,
"description": "Can read security information and reports in Azure AD and Office 365.",
"displayName": "Security Reader"
},
{
"id": "194ae4cb-b126-40b2-bd5b-6091b380977d",
"deletedDateTime": null,
"description": "Security Administrator allows ability to read and manage security configuration and reports.",
"displayName": "Security Administrator"
},
{
"id": "e8611ab8-c189-46e8-94e1-60213ab1f814",
"deletedDateTime": null,
"description": "Can manage role assignments in Azure AD, and all aspects of Privileged Identity Management.",
"displayName": "Privileged Role Administrator"
},
{
"id": "3a2c62db-5318-420d-8d74-23affee5d9d5",
"deletedDateTime": null,
"description": "Can manage all aspects of the Intune product.",
"displayName": "Intune Administrator"
},
{
"id": "158c047a-c907-4556-b7ef-446551a6b5f7",
"deletedDateTime": null,
"description": "Can create and manage all aspects of app registrations and enterprise apps except App Proxy.",
"displayName": "Cloud Application Administrator"
},
{
"id": "5c4f9dcd-47dc-4cf7-8c9a-9e4207cbfc91",
"deletedDateTime": null,
"description": "Can approve Microsoft support requests to access customer organizational data.",
"displayName": "Customer LockBox Access Approver"
},
{
"id": "44367163-eba1-44c3-98af-f5787879f96a",
"deletedDateTime": null,
"description": "Can manage all aspects of the Dynamics 365 product.",
"displayName": "Dynamics 365 Administrator"
},
{
"id": "a9ea8996-122f-4c74-9520-8edcd192826c",
"deletedDateTime": null,
"description": "Can manage all aspects of the Power BI product.",
"displayName": "Power BI Administrator"
},
{
"id": "b1be1c3e-b65d-4f19-8427-f6fa0d97feb9",
"deletedDateTime": null,
"description": "Can manage conditional access capabilities.",
"displayName": "Conditional Access Administrator"
},
{
"id": "4a5d8f65-41da-4de4-8968-e035b65339cf",
"deletedDateTime": null,
"description": "Can read sign-in and audit reports.",
"displayName": "Reports Reader"
},
{
"id": "790c1fb9-7f7d-4f88-86a1-ef1f95c05c1b",
"deletedDateTime": null,
"description": "Can read messages and updates for their organization in Office 365 Message Center only.",
"displayName": "Message Center Reader"
},
{
"id": "7495fdc4-34c4-4d15-a289-98788ce399fd",
"deletedDateTime": null,
"description": "Can manage all aspects of the Azure Information Protection product.",
"displayName": "Azure Information Protection Administrator"
},
{
"id": "38a96431-2bdf-4b4c-8b6e-5d3d8abac1a4",
"deletedDateTime": null,
"description": "Can access and manage Desktop management tools and services.",
"displayName": "Desktop Analytics Administrator"
},
{
"id": "4d6ac14f-3453-41d0-bef9-a3e0c569773a",
"deletedDateTime": null,
"description": "Can manage product licenses on users and groups.",
"displayName": "License Administrator"
},
{
"id": "7698a772-787b-4ac8-901f-60d6b08affd2",
"deletedDateTime": null,
"description": "Full access to manage devices in Azure AD.",
"displayName": "Cloud Device Administrator"
},
{
"id": "c4e39bd9-1100-46d3-8c65-fb160da0071f",
"deletedDateTime": null,
"description": "Allowed to view, set and reset authentication method information for any non-admin user.",
"displayName": "Authentication Administrator"
},
{
"id": "7be44c8a-adaf-4e2a-84d6-ab2649e08a13",
"deletedDateTime": null,
"description": "Allowed to view, set and reset authentication method information for any user (admin or non-admin).",
"displayName": "Privileged Authentication Administrator"
},
{
"id": "baf37b3a-610e-45da-9e62-d9d1e5e8914b",
"deletedDateTime": null,
"description": "Can manage calling and meetings features within the Microsoft Teams service.",
"displayName": "Teams Communications Administrator"
},
{
"id": "f70938a0-fc10-4177-9e90-2178f8765737",
"deletedDateTime": null,
"description": "Can troubleshoot communications issues within Teams using advanced tools.",
"displayName": "Teams Communications Support Engineer"
},
{
"id": "fcf91098-03e3-41a9-b5ba-6f0ec8188a12",
"deletedDateTime": null,
"description": "Can troubleshoot communications issues within Teams using basic tools.",
"displayName": "Teams Communications Support Specialist"
},
{
"id": "69091246-20e8-4a56-aa4d-066075b2a7a8",
"deletedDateTime": null,
"description": "Can manage the Microsoft Teams service.",
"displayName": "Teams Administrator"
},
{
"id": "eb1f4a8d-243a-41f0-9fbd-c7cdf6c5ef7c",
"deletedDateTime": null,
"description": "Has administrative access in the M365 Insights app.",
"displayName": "Insights Administrator"
},
{
"id": "ac16e43d-7b2d-40e0-ac05-243ff356ab5b",
"deletedDateTime": null,
"description": "Can read security messages and updates in Office 365 Message Center only.",
"displayName": "Message Center Privacy Reader"
},
{
"id": "6e591065-9bad-43ed-90f3-e9424366d2f0",
"deletedDateTime": null,
"description": "Can create and manage all aspects of user flows.",
"displayName": "External ID User Flow Administrator"
},
{
"id": "0f971eea-41eb-4569-a71e-57bb8a3eff1e",
"deletedDateTime": null,
"description": "Can create and manage the attribute schema available to all user flows.",
"displayName": "External ID User Flow Attribute Administrator"
},
{
"id": "aaf43236-0c0d-4d5f-883a-6955382ac081",
"deletedDateTime": null,
"description": "Can manage secrets for federation and encryption in the Identity Experience Framework (IEF).",
"displayName": "B2C IEF Keyset Administrator"
},
{
"id": "3edaf663-341e-4475-9f94-5c398ef6c070",
"deletedDateTime": null,
"description": "Can create and manage trust framework policies in the Identity Experience Framework (IEF).",
"displayName": "B2C IEF Policy Administrator"
},
{
"id": "be2f45a1-457d-42af-a067-6ec1fa63bc45",
"deletedDateTime": null,
"description": "Can configure identity providers for use in direct federation.",
"displayName": "External Identity Provider Administrator"
},
{
"id": "e6d1a23a-da11-4be4-9570-befc86d067a7",
"deletedDateTime": null,
"description": "Creates and manages compliance content.",
"displayName": "Compliance Data Administrator"
},
{
"id": "5f2222b1-57c3-48ba-8ad5-d4759f1fde6f",
"deletedDateTime": null,
"description": "Creates and manages security events.",
"displayName": "Security Operator"
},
{
"id": "74ef975b-6605-40af-a5d2-b9539d836353",
"deletedDateTime": null,
"description": "Can manage settings for Microsoft Kaizala.",
"displayName": "Kaizala Administrator"
},
{
"id": "f2ef992c-3afb-46b9-b7cf-a126ee74c451",
"deletedDateTime": null,
"description": "Can read everything that a global admin can read but not update anything.",
"displayName": "Global Reader"
},
{
"id": "0964bb5e-9bdb-4d7b-ac29-58e794862a40",
"deletedDateTime": null,
"description": "Can create and manage all aspects of Microsoft Search settings.",
"displayName": "Search Administrator"
},
{
"id": "8835291a-918c-4fd7-a9ce-faa49f0cf7d9",
"deletedDateTime": null,
"description": "Can create and manage the editorial content such as bookmarks, Q and As, locations, floorplan.",
"displayName": "Search Editor"
},
{
"id": "966707d0-3269-4727-9be2-8c3a10f19b9d",
"deletedDateTime": null,
"description": "Can reset passwords for non-administrators and Password Administrators.",
"displayName": "Password Administrator"
},
{
"id": "644ef478-e28f-4e28-b9dc-3fdde9aa0b1f",
"deletedDateTime": null,
"description": "Can manage all aspects of printers and printer connectors.",
"displayName": "Printer Administrator"
},
{
"id": "e8cef6f1-e4bd-4ea8-bc07-4b8d950f4477",
"deletedDateTime": null,
"description": "Can manage all aspects of printers and printer connectors.",
"displayName": "Printer Technician"
},
{
"id": "0526716b-113d-4c15-b2c8-68e3c22b9f80",
"deletedDateTime": null,
"description": "Can create and manage all aspects of authentication methods and password protection policies.",
"displayName": "Authentication Policy Administrator"
},
{
"id": "fdd7a751-b60b-444a-984c-02652fe8fa1c",
"deletedDateTime": null,
"description": "Members of this role can create/manage groups, create/manage groups settings like naming and expiration policies, and view groups activity and audit reports.",
"displayName": "Groups Administrator"
},
{
"id": "11648597-926c-4cf3-9c36-bcebb0ba8dcc",
"deletedDateTime": null,
"description": "Can create and manage all aspects of Microsoft Dynamics 365, PowerApps and Microsoft Flow.",
"displayName": "Power Platform Administrator"
},
{
"id": "e3973bdf-4987-49ae-837a-ba8e231c7286",
"deletedDateTime": null,
"description": "Can manage Azure DevOps organization policy and settings.",
"displayName": "Azure DevOps Administrator"
},
{
"id": "8ac3fc64-6eca-42ea-9e69-59f4c7b60eb2",
"deletedDateTime": null,
"description": "Can manage AD to Azure AD cloud provisioning and federation settings.",
"displayName": "Hybrid Identity Administrator"
},
{
"id": "2b745bdf-0803-4d80-aa65-822c4493daac",
"deletedDateTime": null,
"description": "Can manage Office apps cloud services, including policy and settings management, and manage the ability to select, unselect and publish 'what's new' feature content to end-user's devices.",
"displayName": "Office Apps Administrator"
},
{
"id": "d37c8bed-0711-4417-ba38-b4abe66ce4c2",
"deletedDateTime": null,
"description": "Can manage network locations and review enterprise network design insights for Microsoft 365 Software as a Service applications.",
"displayName": "Network Administrator"
},
{
"id": "31e939ad-9672-4796-9c2e-873181342d2d",
"deletedDateTime": null,
"description": "Can view and share dashboards and insights via the M365 Insights app.",
"displayName": "Insights Business Leader"
},
{
"id": "3d762c5a-1b6c-493f-843e-55a3b42923d4",
"deletedDateTime": null,
"description": "Can perform management related tasks on Teams certified devices.",
"displayName": "Teams Devices Administrator"
},
{
"id": "c430b396-e693-46cc-96f3-db01bf8bb62a",
"deletedDateTime": null,
"description": "Can create and manage all aspects of attack simulation campaigns.",
"displayName": "Attack Simulation Administrator"
},
{
"id": "9c6df0f2-1e7c-4dc3-b195-66dfbd24aa8f",
"deletedDateTime": null,
"description": "Can create attack payloads that an administrator can initiate later.",
"displayName": "Attack Payload Author"
},
{
"id": "75934031-6c7e-415a-99d7-48dbd49e875e",
"deletedDateTime": null,
"description": "Can see only tenant level aggregates in Microsoft 365 Usage Analytics and Productivity Score.",
"displayName": "Usage Summary Reports Reader"
},
{
"id": "b5a8dcf3-09d5-43a9-a639-8e29ef291470",
"deletedDateTime": null,
"description": "Can configure knowledge, learning and other intelligent features.",
"displayName": "Knowledge Administrator"
},
{p
"id": "744ec460-397e-42ad-a462-8b3f9747a02c",
"deletedDateTime": null,
"description": "Has access to topic management dashboard and can manage content.",
"displayName": "Knowledge Manager"
},
{
"id": "8329153b-31d0-4727-b945-745eb3bc5f31",
"deletedDateTime": null,
"description": "Can manage domain names in cloud and on-premises.",
"displayName": "Domain Name Administrator"
},
{
"id": "31392ffb-586c-42d1-9346-e59415a2cc4e",
"deletedDateTime": null,
"description": "Can create or update Exchange Online recipients within the Exchange Online organization.",
"displayName": "Exchange Recipient Administrator"
}
]
}








你好,在getuser的时候返回error是什么原因呢?
“error”: {
“code”: “Authorization_RequestDenied”,
“message”: “Insufficient privileges to complete the operation.”,
以下三个权限也都给了的。
Directory.ReadWrite.All
User.ReadWrite.All
RoleManagement.ReadWrite.Directory
谢谢!